WPA2 is fallen, winter is here
 drasnor
Starship OperatorHawthorne, CA Icrontian
drasnor
Starship OperatorHawthorne, CA Icrontian
Proving once again that hackers security researchers are the reason we can't have nice things, the Key Installation Attack (KRACK) is loose in the wild and exploits an intrinsic weakness in the WPA2 protocol to let unsavory sorts do unsavory things.
How screwed are you?
That depends on who lives near you and how much you've pissed them off because as usual hacking WiFi networks requires the attacker to be physically close. On the down side, the short story is that there are no more secure wireless protocols.
- WPA2 GCMP, WPA2/WPA TKIP: attackers can decrypt your packets, steal your network key, and spoof your clients to switch to their access point for other nefarious man-in-the-middle attacks
- WPA2 CCMP/AES: attackers can decrypt your packets and spoof your clients to switch to their access point but can't steal your network key.
- WEP: completely cracked years ago, you are better off using WPA2 CCMP/AES.
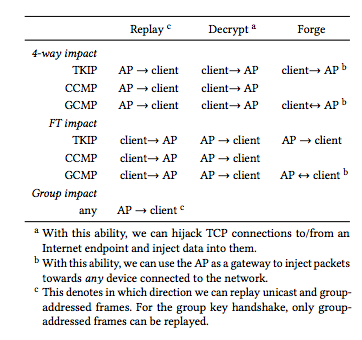
The industrial and national espionage opportunities are more compelling than Eve going after Alice and Bob's home network traffic so some of you are more screwed than others. Authenticated WPA2 Professional still relies on the same underlying technology that has this intrinsic flaw. Additionally, some implementations are more susceptible to certain classes of attacks than others.
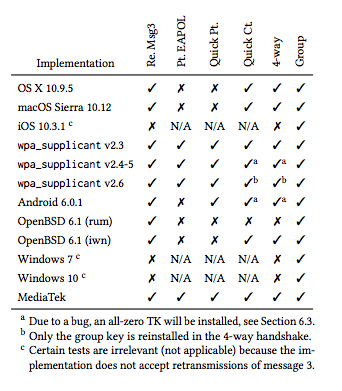
Problematically, the extremely-vulnerable wpa_supplicant implementation is at the heart of any Linux-based system including and especially embedded ones such as consumer WiFi routers, smart TVs, and pretty much any Internet of Things device. For a lot of these things you'll be lucky to ever see a firmware update.
The good news
This can be fixed by a minor revision to the WPA2 specification that's backwards-compatible with existing devices/software/whatever. Network traffic that's designed to operate over unsecure links is unaffected (e.g. https://, encrypted VPN). Read a Mickens about security and feel better.
The bad news
Any fix will require a patch, a lot of stuff won't get patched, and any unpatched device/software/whatever is an attack vector. Unsecure network services (e.g. everything not designed to operate on the raw Internet) are exposed to attackers on your network. An attacker on your network can turn all your stuff into zombies, access your open network shares, and otherwise do anything that someone you've given your network password can do.
Closing thoughts
Have a nice day, patch all your stuff, and don't forget to use AES.






Comments
The real question on everyone's mind now, I think is: "Can I use this information to get free wi-fi on airplanes?"
OpenWRT’s LEDE branch will have a fix in their next service release (17.01.4)
https://forum.lede-project.org/t/lede-v17-01-3-service-release/7113/18
I've read elsewhere that this only affected clients, not routers. Is that true? My desktops are all patched, we all know how ridiculous the Android system is for patches ¯\_(ツ)_/¯, but I'm wondering if I need to be worried about the router or not.
EDIT: I was wrong, it is a client side issue primarily... but mitigations can be put in place on the AP side (from what I'm reading) to detect that a client is being attacked and force them to reauthenticate. Or something like that.
I'm so glad I upgraded my WiFi kit to Ubiquiti gear. They already have a patch rolled.
Good to know, also on the ubiquiti train. Choochoo.
I guess I should update my Ubiquity AP tonight.
I just did a quick controller backup and started the upgrade on everything.
So I could not care less if someone sees my YouTube history or gaming schedules but if I understand correctly someone could use my network to do bad thing which I would then probably be liable for.
My question is, is not broadcasting my ssid a step in the right direction? Pretty positive my neighbors are not going to hack my network but if someone is trolling around my hood, is it at least logical to think if they can not see my network, than the chance of them attacking is lowered?
Marginally lowered. If someone is wardriving your neighborhood though, a hidden SSID is probably not going to be much of a barrier to entry for them.
Someone tell me why certain WiFi devices are only vulnerable in bridge mode.
For the same reason that it is clients which need to be patched. Bridge mode is causing the router to act as a client to another router, and is subject to the same vulnerabilities in the protocol that a client would be. Why some and not all is not known to me at the moment, but it probably has to do with how they chose to implement the WPA2 spec for that particular device.
What source said that the WPA2 password is compromised? The author said, "Our attacks do not recover the password of the Wi-Fi network."
Great summary though. Will be interesting to see the effects.
Good point. Hadn't thought of bridge mode as a client.
My interpretation from the Ars article cited at the beginning.
@drasnor I think both those message keys are temporary. That corresponds with what the analyses seem to be saying: that the attacker is able to decrypt and insert themself into an established client-AP session, but not handshake into the network properly (which requires the password).
I could be wrong. The IEEE offers the 802.11ac spec PDF for the low price of $246 ?
I think that you're probably right that the attacker would become a man-in-the-middle under most circumstances and not a fully-fledged client on their own. I'm not certain that that makes a huge difference in impact though if you can fake being that client to the AP and vice versa.